Bloc B-Apt 1, Résidence les jasmins. Avenue de Dollar - Les berges du Lac II
-
-
-
Mon - Fri 8.00 am - 6.00 pm
Bloc B-Apt 1, Résidence les jasmins. Avenue de Dollar - Les berges du Lac II
Mon - Fri 8.00 am - 6.00 pm

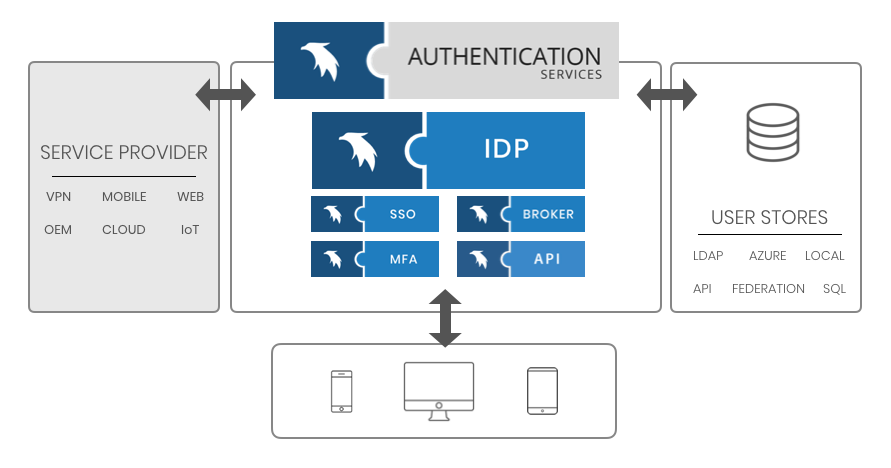
Federation is linking of trust and identities across organizations and for the end user the possibility for Single Sign-On (SSO)
Allows a central point of identity management:
– Enforce strong authentication methods, such as MFA or certificate. Read about the methods here
– Local authentication can be used i.e Active Directory SSO
– Can do context based authentication (internal/external networks, browser type, etc.)
– Restrict access based on group membership, time or days of week, etc.
– No need to manage accounts on remote services when an employee leaves the company.
Please click the following link for the different standard protocols that are supported.
The self enrolment portal for strong authentication is available so the user can enroll to the PhenixID mobile app One Touch. Read more about it here.
Now also available on Apple Watch
Enrollment portal for handling of tokens

After a successful strong authentication it is possible to allow the user to reset/change their password from PhenixID Password Self Service. Read more about it here.

The OpenID Foundation enables organisations to be certified to specific conformance profiles to promote interoperability among implementations.
PhenixID have achieved certifications for these OpenID Provider conformance profiles:

The purpose of oAuth is delegated authentication where you, the end user, authorizes an application to log in as you to another application without giving out your password.
Transforms of a security token from one format to another format, or the federation of an identity from one realm to an equivalent identity in another realm.
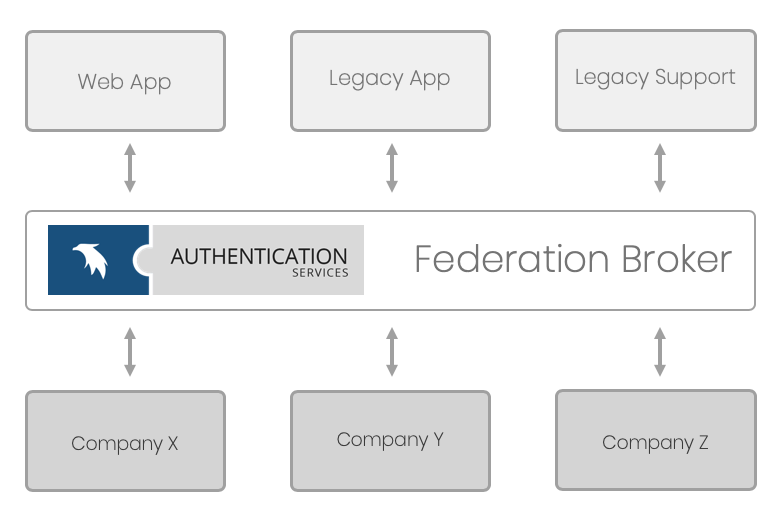
The main purpose of the federation broker is to:
Facilitate for Service providers (applications)
– One connection point (the broker)
– Multiple identity providers connected to the broker.
– Selection list of connected IdP´s (“Please select the organization you belong to”) is provided by the broker
– Central point for maintaining access rules.
Facilitate for Identity providers (organizations)
– One connection point (the broker)
– Multiple service providers connected to the broker.
MyApps is a portal that displays available apps for me. The application displayed is based on authorization criteria i.e. member of group, specific attribute, IP/geolocation etc.
Application icons displayed in MyApps give the user SSO if the application supports federation.
The Solution is built on standards including SAML 2.0, Open IDConnect, ADFS etc.

In many case the Service Desk organisation need to help users calling in by phone.
The Verify User application adds an extra security layer so that the service desk personnel can have a higher trust that they are talking to a legitimate user.
The YouTube movie will showcase a scenario where a service desk personnel have a user contact by mobile phone.
Before helping the user, a verification challenge must be correctly answered by the user.
Several verification options can be used depending on the called in users available methods.
The movie will show the web interface for the service desk personnel and the called in users mobile phone.

© Copyright 2023 PEAKFLOW. All Rights Reserved. POWERED BY GUENTECH