Bloc B-Apt 1, Résidence les jasmins. Avenue de Dollar - Les berges du Lac II
-
-
-
Mon - Fri 8.00 am - 6.00 pm
Bloc B-Apt 1, Résidence les jasmins. Avenue de Dollar - Les berges du Lac II
Mon - Fri 8.00 am - 6.00 pm

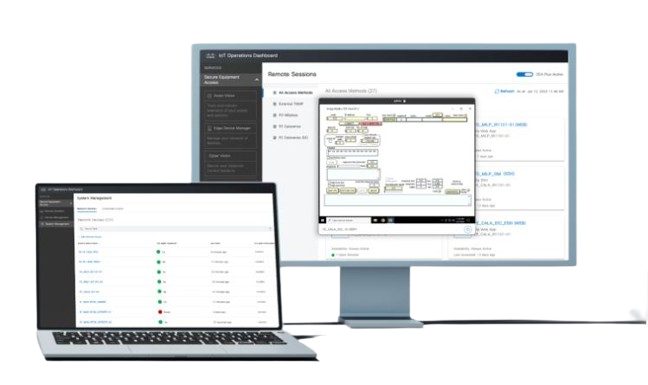
Securing remote access to operational technology (OT) assets has never been easier—or more scalable. Operate with better efficiency and get peace of mind with Cisco Secure Equipment Access.

© Copyright 2023 PEAKFLOW. All Rights Reserved. POWERED BY GUENTECH